Understanding the Trusted Platform Module (TPM) : From Version 1.2 to 2.0 and Beyond

Introduction
The Trusted Platform Module (TPM) has become a crucial element in modern computer security. Developed to secure information on computing devices, it is particularly relevant in the context of increasing security requirements and operating system updates like Windows 11.
TPM Versions: 1.2 vs 2.0
TPM 1.2, introduced in 2003, established the foundation for hardware encryption technology. It has been widely used for device and data security. In contrast, TPM 2.0, launched in 2014, offers increased flexibility and security, thanks to improved cryptography and deeper system integration.
Hardware and Software Updates
Updating TPM hardware may require physical replacement in older systems, while software updates, such as firmware updates, are essential to maintain security and compatibility with the latest standards.
Precautions
Losing TPM keys can lead to irreversible consequences, including the loss of access to encrypted data. Therefore, careful management and backup of keys are crucial.
Impact on Computer Performance
Although TPM can slightly affect performance, especially during intensive encryption processes, this impact is generally minimal compared to the security benefits it offers.
Use for Hard Drive Encryption
TPM plays a key role in hard drive encryption, particularly with technologies like BitLocker. It ensures enhanced security without significantly compromising performance.
Advantages and Disadvantages
Advantages include improved data security and integration with cutting-edge technologies. However, cost, complexity, and some compatibility issues pose challenges.
Importance for Migrating to Windows 11
With Windows 11, TPM 2.0 is a minimum requirement, highlighting the importance of this technology in modern operating systems for enhanced security.
Checking and Updating TPM in Windows
To check the presence and version of the TPM on a Windows machine:
- Open the “Run” tool (Windows key + R).
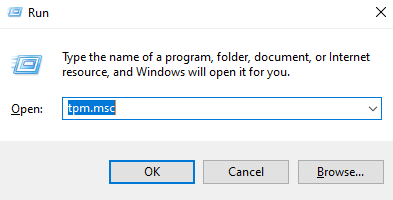
- Type tpm.msc and press Enter. This opens the TPM management console, where you can see if the TPM is present and its version.

To update TPM in Windows, follow the instructions from the TPM manufacturer and your machine’s builder, which generally involve a firmware update via the BIOS or a dedicated utility.
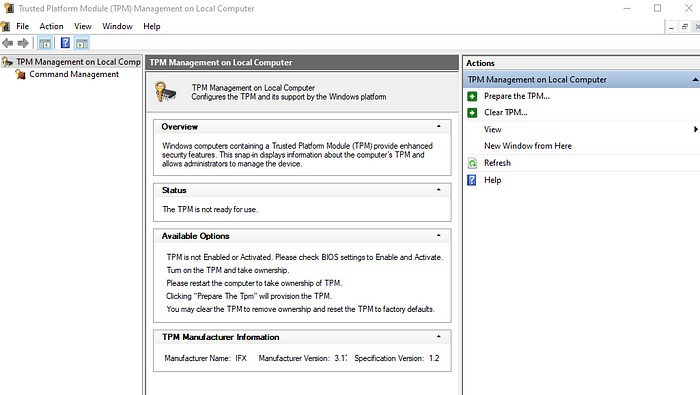
Preparing the TPM Module
Before using the TPM, it may be necessary to initialize or “prepare” it. This step often involves ensuring that the TPM is enabled in the BIOS and that the operating system is configured to use the TPM.
Using TPM in Linux
In Linux, TPM can be used for tasks such as disk encryption via LUKS (Linux Unified Key Setup) or to enhance the security of boot processes. Modern Linux distributions generally include support for TPM 2.0.
Conclusion
TPM continues to be a vital component in computer security. Its evolution and integration into operating systems, both under Windows and Linux, attest to its growing importance.
